A password manager maker is trying to encourage software developers to adopt more secure secrets management with some new features added to its flagship product.
Launched under the name Developer Tools, 1Password declared the new features will help developers easily and securely generate, manage and access secrets in their normal workflows.
The tools will also help simplify complex processes and improve security practices to ensure data is protected, without slowing down the development pipeline, it added, as well as provide developers with secure access to the secrets they need wherever they are, regardless of the device they are using.
“Historically, one of the biggest constraints to secure coding and operations was tools to securely manage secrets — the passwords and keys that are needed to securely interconnect components,” observed Casey Bisson, head of product and developer relations at BluBracket, a provider of code security solutions in Palo Alto, Calif.
“In too many cases,” he told TechNewsWorld, “these secrets are being stored in code. But a secret in code is a secret told.”
Citing a study by 1Password, its Chief Product Officer and General Manager of Emerging Solutions Akshay Bhargava told TechNewsWorld that one in four employees at IT DevOps companies have secrets in 10 or more locations and have shared them with colleagues using insecure channels, such as in an email or Slack message.
He added that one in three IT DevOps workers say they will share secrets over insecure channels, if it helps them get their work done faster.
What’s more, he continued, 61 percent of projects are delayed due to poor secrets management.
Easy SSH Key Management
The new features in the Developer Tools offering include SSH key management, which allows developers to store and use SSH keys with just a few clicks.
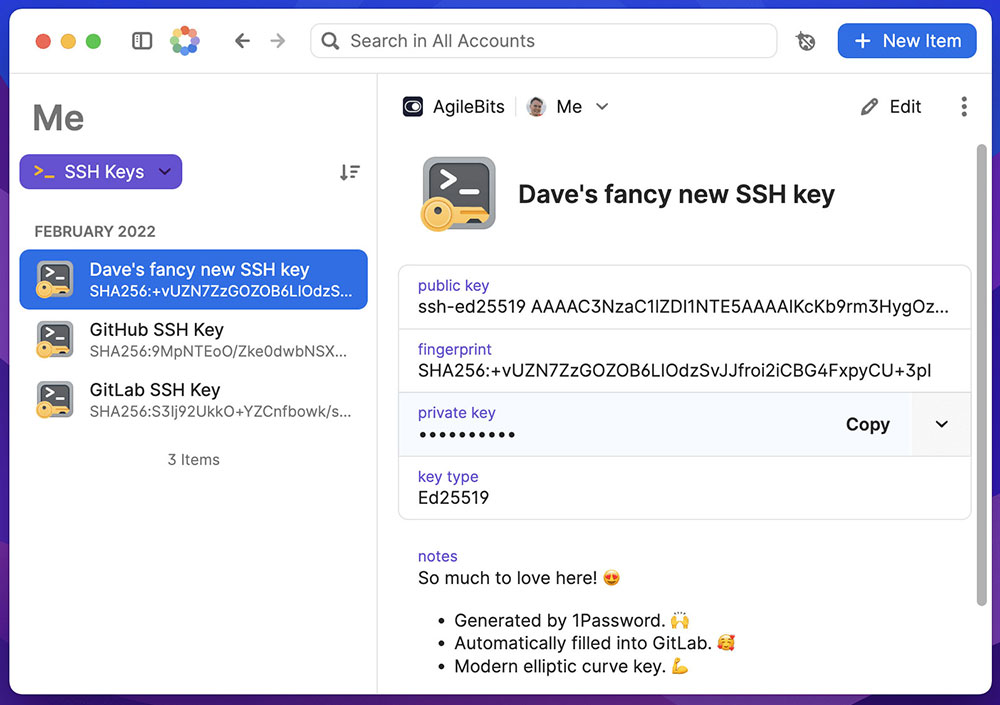
To help avoid errors, 1Password for the browser will autofill a developer’s public keys into popular sites, including GitHub, GitLab, BitBucket and Digital Ocean.
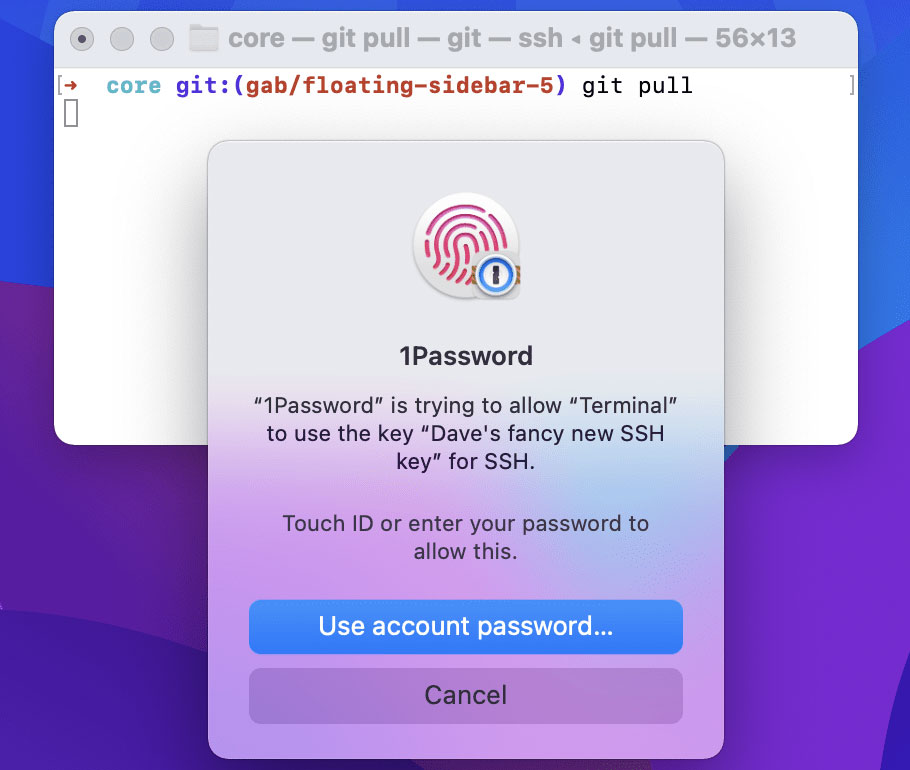
Then, with a built-in SSH agent, users can push code to GitHub and authenticate other SSH workflows in a terminal by simply scanning their fingerprints, increasing security with less effort.
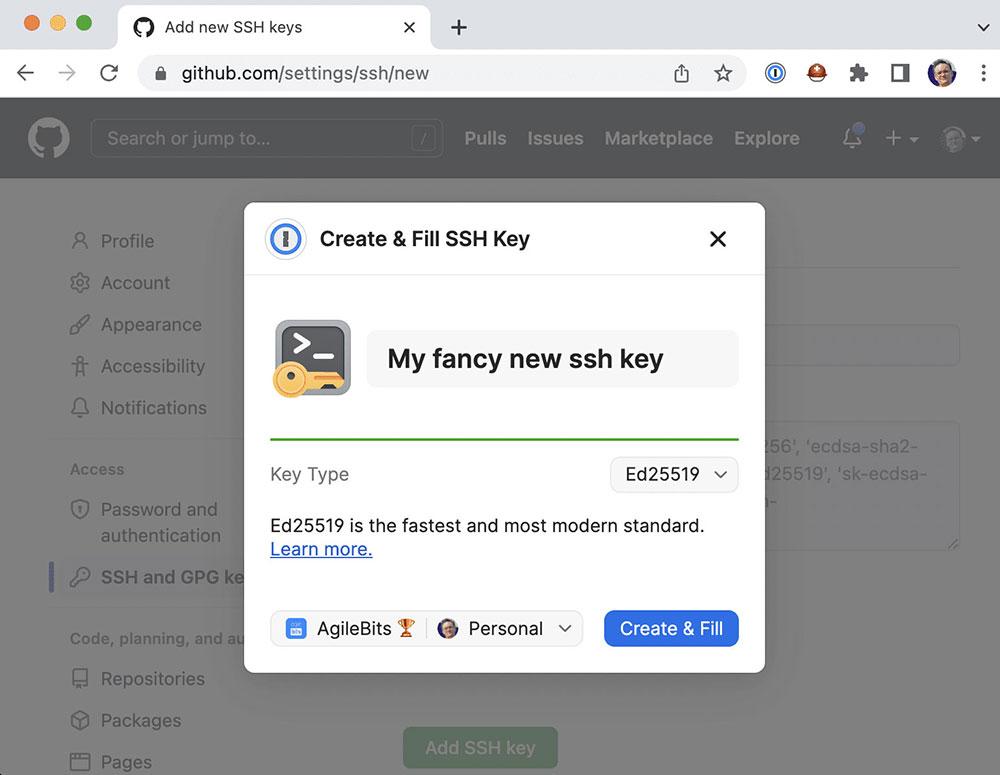
Developers no longer need to remember or type key passphrases, manually copy keys to new devices, or store files on their disk, thereby avoiding weak encryption of SSH keys and other security risks.
“All the hassle of exchanging keys on different machines, adding and removing keys from the agent, entering passphrases from keys, is now just one biometric authentication,” Marcel Kersten, a software Developer at ComLine GmbHd, said in a statement.
New CLI and Secrets Vault
A new command line interface, with improved syntax and a new biometric unlock, allows developers to quickly manage secrets, provision users or automate workflows in a terminal without switching from their development tools or manually typing passwords.
Developer Tools also simplifies key management with CLI inject and run commands, allowing developers to code with secret references that are substituted for actual API keys from their vault at runtime.
“The new 1Password CLI allowed our web development team to save time synchronizing passwords and API keys in a much more secure manner than previously possible,” Craig Haseler, a project manager at TechSource, said in a statement.
“I’d strongly recommend any web development team look into using the 1Password CLI tools to boost security and efficiency,” he added.
Encrypted vaults for storing secrets so instead of hardcoding them or storing them as unsecure plaintext, in configuration files or in spreadsheets, developers can manage and access their secrets in one place within their preferred tools and workflows.
Storing secrets in encrypted vaults, and as one of several default item types — API credential, AWS account, database, server, or SSH key — will help prevent breaches caused by leaked secrets.
Developer Tools also facilitates collaboration by providing secure access to secrets across a team.
Discouraging Shortcuts
The new tools by 1Password aim to encourage better secrets management by developers and discourage them from cutting corners that can create security risks.
“It’s not so much cutting corners, as finding a way to work within imposed deadlines and trying to be efficient as possible,” explained Daniel Kennedy, research director for information security and networking, at 451 Research, which is part of S&P Global Market Intelligence.
“Organizations install all manner of well-intentioned processes, code scanning, and other application testing tools, and if they create a lot of friction in developers’ daily lives, to the point where they think the burden outweighs the value, they have a lot of agency, sometimes hidden agency, to work around these impediments,” he told TechNewsWorld.
“Developers aren’t paid to deliver security. They are paid to deliver features,” added John Bambenek, principal threat hunter at Netenrich, an IT and digital security operations company in San Jose, Calif.
“Often they operate on tight timelines to rush to market which means any delay, even for security, can be left by the wayside,” he told TechNewsWorld.
Lipstick on a Security Pig
Traditionally, security has been seen as slowing down developers. “This doesn’t have to be the case and newer vendors — true DevSecOps vendors — have figured this out and developers love using them because they actually speed up development not slow them down,” observed Larry Maccherone, DevSecOps transformation evangelist at Contrast Security, a maker of self-protecting software solutions in Los Altos, Calif.
“However, most security tool vendors are just DevOps lipstick on a traditional security pig,” he told TechNewsWorld.
DevSecOps has created a sense of shared responsibility in the development universe, maintained Josh Bressers, vice president of security at Anchore, a software development security company in Santa Barbara, Calif.
“If you look at more traditional development models, you had development, you had testing, you had security, you had all these different groups with slightly different goals.” he told TechNewsWorld. “Whenever you have different groups with different goals, you get different results. In DevSecOps, where you have shared responsibility, the goals are more aligned.”
“When you consider how most companies originally approached creating secure code, which was doing scans against huge code bases and then massive clean-up projects, we’ve come a long way,” Kennedy added.
“Having security arrive as a project is about to go into production with hundreds of vulnerabilities to clean up isn’t an effective approach to application security,” he continued. “If scans can be done incrementally at appropriate points in a development pipeline, that’s a much lower friction way to ensure applications are being created and updated with due consideration to security.”























































